ECC collision HOWTO
This is a small blog post I would have been happy to read while searching how to find ecc collision when dealing with how to exploit a limited write to flash.
No rocket science, just a little write-up.
more...This is a small blog post I would have been happy to read while searching how to find ecc collision when dealing with how to exploit a limited write to flash.
No rocket science, just a little write-up.
more...In this post, I will show you how I bypassed a noexec permission in a limited chrooted env.
more...The stm32wb55 mcu is a dual core (cortex-m4/cortex-m0) mcu with integrated wireless capabilities (ble/thread/zigbee).
more...
A few months back, I turned my attention on my fiber gateway. So I ordered the same model on ebay, unsoldered and dump the nand, and after a lot of work, managed to have a clear view of the system, from bootloader to userland.
Basically, the bootloader check the signature of the kernel image, uncrypt the kernel image with a bootloader stored key, which in turn, uncrypt the rootfs image and voila.
[YYYY] / # ls README dev lib opt sbin usr bin etc media proc sys var config exports mnt root tftpboot ctmp home nonexisting run tm [YYYY] / # cat README If you can read this, congratulations ! Feel free to drop me an email, xxxx@yyyy.zz
The percello prc6000, also known as bcm61650 after Broadcom bought the company, is a chip used in 3g femtocells (Home-nodeB).
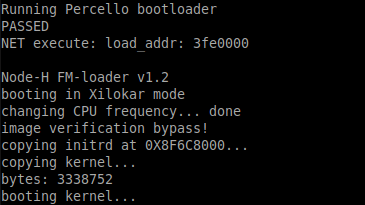
Here is a summary writeup of how I achieved to bypass its secure ROM to run arbitrary firmwares.
more...A picture is worth a thousand words...
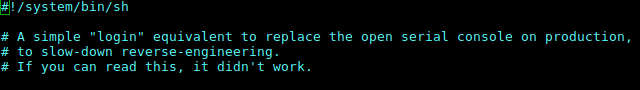
Found this old piece of code, written in 2013. Only needed to change hardcoded resolution of the webcam to get it working again.
#include <stdio.h>
int main(int argc, char** argv) {
printf("Hello World\n");
return 0;
}
Page 1 / 1